When the unlocking method is password, card, or face, the interaction process is shown in the following figure:
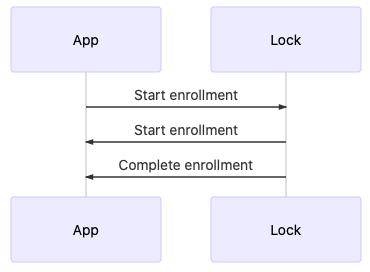
When the unlocking method is the fingerprint, the interaction process is shown in the following figure:
This topic describes the data point (DP) function, frame format, and usage method involved in the Tuya Smart Bluetooth door lock application. It applies to the public version of the Bluetooth door lock project.
The following table lists some terms and definitions involved in this topic. For more details, see Terms.
| Term | Definition |
|---|---|
| DP | One data point (DP) refers to one function, one command, or one pair of commands. |
| PID | Product ID. It describes the collection of one type of product function (DP). Every product that is created on the Tuya IoT Console will have a unique product ID (PID). PID is associated with all information related to this product, including specific DP, app control panel, and delivery information. |
| UUID | A universally unique identifier (UUID) is the SDK license and unique ID when you develop a smart product on the IoT Console of Tuya Smart. A UUID is a 20-digit number. |
| authkey | Authkey is the authentication key to register the device to the cloud. One authkey corresponds to one UUID. An authkey is a 32-digit number. |
| Firmware key | The unique identification of the firmware on the Tuya Console. |
| Member | Member is also called “user”. They are the same. |
| Member ID | A 1-byte unsigned integer. It refers to the member number (also known as the user number), which is distributed by the server and does not need to be maintained locally. The value range is 0x01 to 0x64. Others are reserved values. |
| Hardware ID | 1-byte unsigned integer. It refers to the hardware number related to the unlocking method, which is allocated and maintained locally. Each unlocking method corresponds to a hardware ID. For example, fingerprint-hardware ID is 0x01, and password-hardware ID is 0x02. The value range is 0x00 to 0xFE, and 0xFF is a reserved value. |
| Valid time | A specific unlocking method (such as fingerprint or password) is valid within a specified time range. |
| Smart stick lock | A device that upgrades traditional locks to smart locks. Search for details. |
| Send | The direction of data transmission is from the mobile phone/gateway to the Bluetooth device. |
| Report | The direction of data transmission is from the Bluetooth device to the mobile phone/gateway. |
Host: Tuya Smart app
Slave: Bluetooth lock
The host recognizes the slave through Bluetooth broadcasting and initiates a pairing request to the authorized slave. The master and slave that have completed the pairing are in the bound states.
There is a secure channel conforming to the Bluetooth specification between the master and slave in the bound states. All business communications are carried out in this secure channel.
The process of establishing a secure channel can be briefly described as follows: Unbound > Connect > Pair > Bound > Secure communication > Disconnect > Reconnect > Bound > Secure communication > … > Remove > Unbound
When you use Tuya Bluetooth modules for development, the length of dp_data_len is 2 bytes. For information about other DP formats, see the table below:
| Field | Length (byte) | Description |
|---|---|---|
| dp_id | 1 | DP command |
| dp_type | 1 | DP data type |
| dp_data_len | 1 | DP data length |
| dp_data_value | dp_data_len | DP data content |
| Data direction |
dp_id (1 byte) |
DP _type (1 byte) |
dp_da ta_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send |
1 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Valid time (17 bytes) |
Number of times (1 byte) |
Password length (1 byte ) |
Password content (n byte) |
|
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: start enrollment 0xFE: cancel enrollment ( initiated by the app) |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
See Appendix 1 |
Value range |
Description | Description | |||||
| Report |
1 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Number of times (1 byte) |
Return status (1 byte) |
|||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: start enrollment |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
The total number of enrollments. For example, it takes six times to enroll a fingerprint, and once for card enrollment. |
0x00: default | |||||||
| 0xFC: enrollment in progress |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
The serial number of enrollment times. For example, the fingerprint is usually 6 times. Fill in the number each time. (starting from 1) |
Reasons for enrollment exception: 0x00: no exception 0x01: incomplete fingerprint |
||||||||
| 0xFD: enrollment failed |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
Current enrollment phase: 0x00: start enrollment, 0xFC: enrollment in progress, 0xFF: enrollment completed |
Reason for enrollment failure | ||||||||
| 0xFE: canceled (initiate on the app) |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
0x00: default | 0x00: default | ||||||||
| 0xFF: enrollment completed |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0x00 - 0xFE |
0x00: default | 0x00: default | ||||||||
Interactive example
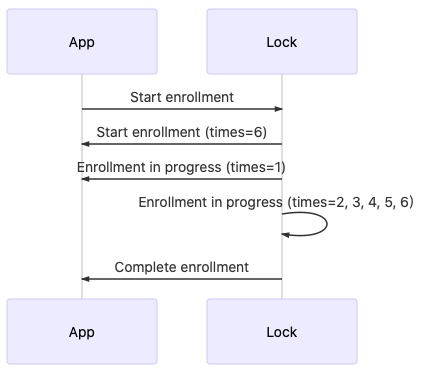
When the unlocking method is password, card, or face, the interaction process is shown in the following figure:

When the unlocking method is the fingerprint, the interaction process is shown in the following figure:

| Data direction |
dp_id (1 byte) |
dp _type (1 byte) |
dp_da ta_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send |
2 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Deletion mode (1 byte) |
||||
| 0x00: delete a member | 0x00: default |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
0x00: delete all the unlocking methods of the member |
||||||||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: default |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0x00 -0xFE |
0x01: delete one of the unlock methods of the member |
||||||||
| Report |
2 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Deletion mode (1 byte) |
Return status (1 byte) |
|||
| 0x00: delete a member | 0x00: default |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default |
0x00: delete all the unlocking methods of the member |
0x00: failed to delete 0xFF: deleted successfully |
|||||||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: default |
0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0x00 -0xFE |
0x01: delete one of the unlock methods of the member |
0x00: failed to delete 0xFF: deleted successfully |
|||||||
| Data direction |
dp_id (1 byte) |
dp_type (1 byte) |
dp_da ta_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send |
3 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Valid time (17 bytes) |
Number of times (1 byte) |
Password length (1 byte ) |
Password content (n byte) |
|
| 0x00: only modify the valid time of a member |
0x00: default | 0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default | See Appendix 1 |
0x00: default (the number of times cannot be modified) |
Description | Description | |||||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: default | 0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0x00-0xFE | See Appendix 1 |
Value range |
Description | Description | |||||
| Report |
3 | raw | len | Type (1 byte) |
Phase (1 byte) |
Administrator tag (1 byte) |
Member ID (1 byte) |
Hardware ID (1 byte) |
Number of times (1 byte) |
Return status (1 byte) |
|||
| 0x00: only modify the valid time of a member |
0x00: default | 0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0xFF: default | 0x00: default (the number of times cannot be modified) |
0x00: failed to modify 0xFF: modified successfully |
|||||||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
0x00: default | 0x00: ordinary member 0x01: administrator |
0x01 -0x64 |
0x00-0xFE | Value range | 0x00: failed to modify 0xFF: modified successfully |
|||||||
Temporary passwords include one-time passwords and periodic passwords. The difference between a temporary password and a normal password is as follows:
Temporary password does not belong to any member.
The valid time of the temporary password can be changed separately in the connected status.
The temporary password is defined as 0xF0 as an unlocking method (0x01 is the password, 0x02 is a card, and 0x03 is fingerprint…)
Risk:
After the network is disconnected, if the device is powered off, the local clock will not work properly. If the network cannot be connected and the clock cannot be synchronized in time, the periodic repetition function of the periodic password will not be accurately judged locally.
Solution:
| Data direction |
dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 51 | raw | len | Type (1 byte) |
Valid time (17 bytes) |
Number of times (1 byte) |
Password length (1 byte) |
Password content (n byte) |
|||||
| 0x00: type 0 00x01: type 1 |
See Appendix 1 | Value range | The byte number of password: n (only used for password type) |
Description | |||||||||
| Report | 51 | raw | len | Hardware ID (1 byte) |
Return status (1 byte) |
||||||||
| 0x00-0xFE | 0x00: added successfully 0x01: failed to add 0x02: all hardware IDs are allocated |
||||||||||||
| Data direction |
dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 52 | raw | len | Hardware ID (1 byte) |
|||||||||
| 0x00-0xFE | |||||||||||||
| Report | 52 | raw | len | Hardware ID (1 byte) |
Return status (1 byte) |
||||||||
| 0x00-0xFE | 0x00: deleted successfully 0x01: failed to delete |
||||||||||||
| Data direction |
dp_id (1 byte) |
DP _type (1 byte) |
dp_da ta_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 53 | raw | len | Hardware ID (1 byte) |
Type (1 byte) |
Valid time (17 bytes) |
Number of times (1 byte) |
Password length (1 byte) |
Password content (n byte) |
||||
| 0x00-0xFE | 0x00: type 0 00x01: type 1 |
See Appendix 1 | Value range | The byte number of password: n (only used for password type) |
Description | ||||||||
| Report | 53 | raw | len | Hardware ID (1 byte) |
Return status (1 byte) |
||||||||
| 0x00-0xFE | 0x00: modified successfully 0x01: failed to modify |
||||||||||||
In order to maintain the consistency between the server and the local unlocking methods of the device, each time you enter the hardware list on the app or pull down to refresh the hardware list interface on the app, you need to perform full synchronization of the unlocking methods (all the unlocking methods added on the phone and locally). The hardware type enumeration is used to notify the local of the hardware type that needs to be synchronized this time. The unsent hardware type does not need to be reported locally. The data length of each packet in synchronization is defined by the user, and the total length of each packet is not more than 200 bytes. For more information, see FAQ.
| Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 54 | raw | len | Hardware type enumeration (len bytes) |
|||||||||
| 0x01: password 0x02: card 0x03: fingerprint 0x04: face |
|||||||||||||
| Report | 54 | raw | len | Phase (1 byte) |
Packet S.N. (1 byte) |
Synchronization data (n bytes) |
|||||||
| 0x00: synchronizing | 0x00-0xFF | Data 1, data 2 ... data n | |||||||||||
| Report | 54 | raw | len | Phase (1 byte) |
Total number of packets (1 byte) |
||||||||
| 0x01: end of synchronization | Total number of packets | ||||||||||||
Old version of synchronizing unlocking methods (which will be deprecated soon)
In order to minimize the amount of data transferred during synchronization, only the differentiated parts are synchronized each time. When you start to synchronize unlocking methods, the app will send the CRC8 value of the hardware ID, hardware type, and properties bound to each hardware ID (such as member ID and frozen status) stored on the server-side to the local device. After receiving the data, the received data and the locally stored data is compared. Then, the differentiated hardware ID is selected, and its property value is uploaded again.
| Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 35 | raw | len | Number of hardware IDs (1 byte) |
Send hardware 1 (3 bytes) |
Send hardware 2 (3 bytes) |
… | Send hardware n (3 bytes) |
|||||
| Number | See the note | See the note | … | See the note | |||||||||
| Report | 35 | raw | len | Number of hardware IDs (1 byte) |
Report hardware 1 (3 bytes) |
Report hardware 2 (3 bytes) |
… | Report hardware n (3 bytes) |
|||||
| Number | See the note | See the note | … | See the note | |||||||||
Note:
CRC8 calculation method: CRC8 is the low byte of CRC16. The C language calculation method of CRC16 is as follows:
uint16_t cpt_crc16_compute(uint8_t* buf, uint16_t size, uint16_t* p_crc)
{
uint16_t poly[2] = {0, 0xa001}; //0x8005 <==> 0xa001
uint16_t crc = 0xffff;
int i, j;
for(j=size; j>0; j--)
{
uint8_t ds = *buf++;
for(i=0; i<8; i++)
{
crc = (crc >> 1) ^ poly[(crc ^ ds) & 1];
ds = ds >> 1;
}
}
return crc;
}
| Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 59 | raw | len | Function (1 byte) |
|||||||||
| 0x00: function 0 00x01: function 1 ... |
|||||||||||||
| Report | 59 | raw | len | Function (1 byte) |
Return status (1 byte) |
||||||||
| 0x00: function 0 00x01: function 1 ... |
0x00: success 0x01: failure |
||||||||||||
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Freeze users | Send/report | 49 | value | len | Member ID (4 bytes) | |||||||||
| 0x01-0x64 | ||||||||||||||
| Unfreeze users | Send/report | 50 | value | len | Member ID (4 bytes) |
|||||||||
| 0x01-0x64 | ||||||||||||||
When the app successfully connects to a Bluetooth lock and unlocks it through the panel, the device unlocks after receiving the request and reports the unlocking record through ID 19.
| Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 6 | raw | len | Function (1 byte) |
Member ID (1 byte) |
||||||||
| 0x00: lock 0x01: unlock |
0x01-0x64 | ||||||||||||
| Report | 6 | raw | len | Return status (1 byte) |
Member ID (1 byte) |
||||||||
| 0x00: failure 0x01: success |
0x01-0x64 | ||||||||||||
| Data direction |
dp_id (1 byte) |
dp_type (1 byte) |
dp_da ta_len (1 byte) |
dp_data_value | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send |
60 | raw | len | Validity (1 byte) |
Member ID (2 bytes) |
Key valid time (4 bytes) |
Key expiration time (4 bytes) |
Key usage times (2 bytes) |
Key content (8 bytes) |
|||
| 0x00: invalid 0x01: valid |
0x01 -0x64 |
Unix timestamp (same as Appendix 1) |
Unix timestamp (same as Appendix 1) |
0x0000 -0xFFFF |
ASCII code | |||||||
| Report |
60 | raw | len | Return status (1 byte) |
Member ID (2 bytes) |
|||||||
| Value range | 0x01 -0x64 |
|||||||||||
Remote unlocking refers to unlocking through the communication link of the gateway:
Note: Either “remote unlocking” or “Bluetooth unlocking”, the unlocking operation must be made. The two unlocking methods are just different in the data link, and the actual business meaning is the same.
| Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data _len (1 byte) |
dp_data_value | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Send | 61 | raw | len | Function (1 byte) |
Member ID (2 bytes) |
Key content (8 bytes) |
Unlocking method (2 bytes) |
|||||
| 0x00: lock 0x01: unlock |
0x01-0x64 | ASCII code | 0x0000: remote unlocking 0x0001: unlocking with mobile phone 0x0002: unlocking with voice |
|||||||||
| Report | 61 | raw | len | Return status (1 byte) |
Member ID (2 bytes) |
|||||||
| Value range | 0x01-0x64 | |||||||||||
| Data direction | dp_ID (1 byte) |
dp_Type (1 byte) |
dp_da ta_Len (1 byte) |
dp_data_value | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Report | 69 | raw | len | The slave ID (2 bytes) |
Action (1 byte) |
|||||||
| 0~10000 | 0x01: The request unlocking record | |||||||||||
| Send | 69 | raw | len | slave ID (2 bytes) |
host ID (2 bytes) |
random number (8 bytes) |
fixed value (1 byte) |
|||||
| 0~10000 | 0~10000 | The host random number | 0x00 | |||||||||
| Data direction | dp_ID (1 byte) |
dp_Type (1 byte) |
dp_da ta_Len (1 byte) |
dp_data_value | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Report | 74 | raw | len | Combination type (1 byte) |
unlock mode - 1 (1 byte) |
Hardware Id-1 (1 byte) |
unlock mode - 2 (1 byte) |
Hardware Id-2 (1 byte) |
||||
| Value range | Value range | 0x01~0xFE | Value range | 0x01~0xFE | ||||||||
The default value of the setting type DP on the panel is specified as follows:
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value |
|---|---|---|---|---|---|
| Doorbell sound effect | Send/report | 26 | enum | len | Sound effect (1 byte) |
| 0x00: sound effect 0 … 0x0A: sound effect 10 |
|||||
| Doorbell volume | Send/report | 27 | enum | len | Volume (1 byte) |
| Value range | |||||
| Key-pressing volume | Send/report | 30 | enum | len | Volume (1 byte) |
| Value range | |||||
| Local navigation volume | Send/report | 31 | enum | len | Volume (1 byte) |
| Value range | |||||
| Language | Send/report | 28 | enum | len | Language (1 byte) |
| Value range | |||||
| Switch between single unlocking and combination unlocking |
Send/report | 34 | enum | len | Possible combinations of unlocking methods (1 byte) |
| Value range | |||||
| Rotation direction of motor of smart stick lock |
Send/report | 48 | enum | len | Rotation direction (1 byte) |
| 0x00: unlock clockwise 0x01: unlock counterclockwise |
|||||
| Torque force of motor | Send/report | 56 | enum | len | Torque force of motor (1 byte) |
| Value range | |||||
| Manual locking | Send | 46 | bool | len | Fixed value (1 byte) |
| 0x01 | |||||
| Report | 46 | bool | len | Return status (1 byte) | |
| 0x00: failure 0x01: success |
|||||
| Arm away | Send/report | 58 | bool | len | Switch (1 byte) |
| 0x00: off 0x01: on |
|||||
| Automatic locking switch | Send/report | 33 | bool | len | Switch (1 byte) |
| 0x00: off 0x01: on |
|||||
| Automatic locking timer | Send/report | 36 | value | len | Timed period (s) (4 bytes) |
| 0x00000001-0xFFFFFFFF | |||||
| Welcome message on the display screen | Send/report | 29 | string | len | Welcome message (len bytes) |
| 0-50 bytes | |||||
| Special functions | Send/report | 68 | enum | len | Function (1 byte) |
| 0x00: function 0 00x01: function 1 ... |
The default value of the status type DP on the panel is specified as follows:
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value |
|---|---|---|---|---|---|
| Battery percentage | Report | 8 | value | len | Percentage (4 bytes) |
| 0x01-0x64 | |||||
| Battery level | Report | 9 | enum | len | Battery level (1 byte) |
| Value range | |||||
| Child lock status | Report | 10 | bool | len | Status (1 byte) |
| 0x00: child lock is disabled 0x01: child lock is enabled |
|||||
| Lifting up and double locking status | Report | 11 | bool | len | Status (1 byte) |
| 0x00: the handle is not lifted up for double locking 0x01: the handle is lifted up for double locking |
|||||
| Double locking status | Send/report | 32 | bool | len | Status (1 byte) |
| 0x00: not double locked 0x01: double locked |
|||||
| Doorbell notification | Report | 24 | bool | len | Fixed value (1 byte) |
| 0x00 | |||||
| Open and closed status | Report | 40 | enum | len | Status (1 byte) |
| 0x00: "unknown" 0x01: "open" 0x02: "closed" |
|||||
| Open and closed status | Report | 47 | bool | len | Status (1 byte) |
| 0x00: the lock is closed 0x01: the lock is opened |
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value | |
|---|---|---|---|---|---|---|
| Unlock with fingerprint | Report | 12 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with password | Report | 13 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with card | Report | 15 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with mechanical key | Report | 16 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with face recognition | Report | 39 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with iris | Report | 41 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with palm print | Report | 42 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with finger vein | Report | 43 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Unlock with temporary password | Report | 55 | value | len | Hardware ID (4 bytes) | |
| 0x00-0xFE | ||||||
| Combination unlock | Report | 57 | enum | len | Possible combinations of unlocking methods (1 byte) |
|
| Value range | ||||||
| Unlock with Bluetooth | Report | 19 | value | len | Member ID (4 bytes) | |
| 0x01-0x64 | ||||||
| Remote unlocking with mobile phone | Report | 62 | value | len | Member ID (4 bytes) | |
| 0x01-0x64 | ||||||
| Remote unlocking with voice | Report | 63 | value | len | Member ID (4 bytes) | |
| 0x01-0x64 | ||||||
| Unlock from the inside of the door | Report | 18 | bool | len | Fixed value (1 byte) | |
| 0x00 | ||||||
| Alert reason | Report | 21 | enum | len | Alert reason (1 byte) | |
| Value range | ||||||
This section introduces other passwords as unlocking methods, including offline passwords and dynamic passwords.
Scenario:
The operator obtains the offline password through APP/SaaS and informs the user.
The user gets a one-time password: if it is used within 6 hours, the door is opened successfully. Then, the password is invalid, and an unlocking record is generated. It becomes invalid after six hours.
The user gets a time-limited password: if it is used once within 24 hours, the password is activated. It can be used within the time limit, and an unlocking record will be generated every time it is used. It becomes invalid if it is not used within 24 hours.
The user gets the notification to clear a one-time password: the validity is the same as the password to be cleared. For multiple uses, only the use of the first time takes effect. A record of “clearing a one-time password” is generated.
The user gets the notification to clear all passwords: if it is used within 24 hours, all passwords will be cleared. It can be used only once. A record of “clearing all passwords” is generated. It becomes invalid after 24 hours.
Restrictions on clearing a one-time password/all passwords:
For usage, see the example code.
The example code is in lock_hard.c file of the SDK installation package.
Both the local lock and the cloud independently have the same set of dynamic password generation algorithms. The only connection between the two is the Unix timestamp. If the difference of Unix timestamp between the lock and the cloud is no more than 300 seconds, the dynamic passwords generated by the two are considered to be the same. Local unlocking is allowed.
The actual implementation mechanism of the dynamic password is slightly different, but the generated result is as described above. The calling method is as follows:
if(DYNAMIC_PWD_VERIFY_SUCCESS == lock_dynamic_pwd_verify(&data[0], 8)) {
APP_DEBUG_PRINTF("lock_open_with_dynamic_pwd_success");
} else{
APP_DEBUG_PRINTF("lock_open_with_dynamic_pwd_fail");
}
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value |
|---|---|---|---|---|---|
| Offline password Set T0 time |
Send/report | 64 | string | len | T0 timestamp string (10 bytes) |
| Unix timestamp string | |||||
| Unlock with offline password | Report | 67 | raw | len | Encrypted unlocking password (16 bytes) |
| See the note | |||||
| Offline password Clear a one-time password |
Report | 65 | raw | len | Encrypted clearing code (16 bytes) |
| See the note | |||||
| Offline password Clear all passwords |
Report | 66 | raw | len | Encrypted clearing code (16 bytes) |
| See the note | |||||
| Unlock with dynamic password | Report | 14 | value | len | Hardware ID (4 bytes) |
| 0xFF: default value |
Note: The encrypted clear code is output.
app_port_aes128_cbc_encrypt(login_key, iv, input, input_len, output);
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value |
|---|---|---|---|---|---|
| SMS notification | None | 25 | bool | len | None |
| Hijack alarm | None | 22 | bool | len | None |
| Hardware clock RTC | None | 44 | bool | len | None |
If your smart door lock needs to support lock accessories, you need to use these DPs. For more information, see the new DP section of DP Protocol of Lock Accessories.
| Function | Data direction | dp_id (1 byte) |
dp_type (1 byte) |
dp_data_len (1 byte) |
dp_data_value |
|---|---|---|---|---|---|
| Configure random number of the host | None | 70 | raw | len | See the above-mentioned link |
| Locking and unlocking | None | 71 | raw | len | |
| Locking and unlocking record | None | 72 | raw | len | |
| Remote unlocking configuration | None | 73 | raw | len |
| Byte | Meaning | Description | Example | |||
|---|---|---|---|---|---|---|
| 1 | Start time of validity | unsigned integer 4 bytes (big endian) |
For example, the Unix time is: 123-456-789 = 0x075BCD15 If it is permanently valid, the start time is 0x386CD300. |
07 | ||
| 2 | 5B | |||||
| 3 | CD | |||||
| 4 | 15 | |||||
| 5 | End time of validity | unsigned integer 4 bytes (big endian) |
For example, the Unix time is: 999-999-999 = 0x3B9AC9FF If it is permanently valid, the end time is 0x72BC9B7F. |
3B | ||
| 6 | 9A | |||||
| 7 | C9 | |||||
| 8 | FF | |||||
| 9 | Validity cycle mode | 0x00: no cycle | 0x01: daily cycle | 0x02: weekly cycle | 0x03: monthly cycle | |
| 10 | Cycle flag bit 1 | Without cycle, 10-17. All bytes are 0 |
This byte is 0x00 by default |
This byte is 0x00 by default |
bit7: 0 by default bit6: No. 31 ... bit0: No. 25 |
|
| 11 | Cycle flag bit 2 | This byte is 0x00 by default |
This byte is 0x00 by default |
bit7: No. 24 … bit0: No. 17 |
||
| 12 | Cycle flag bit 3 | This byte is 0x00 by default |
This byte is 0x00 by default |
bit7: No. 16 … bit0: No. 9 |
||
| 13 | Cycle flag bit 4 | This byte is 0x00 by default |
bit7: 0 by default bit6: Saturday ... bit1: Monday bit0: Sunday |
bit7: No. 8 … bit0: No. 1 |
||
| 14 | Start time of one day 1 (hour) | Start time: 08:30 | 08 (decimal) | |||
| 15 | Start time of one day 2 (minute) | 30 (decimal) | ||||
| 16 | End time of one day 1 (hour) | End time: 20:30 | 20 (decimal) | |||
| 17 | End time of one day 2 (minute) | 30 (decimal) | ||||
When you add or modify the unlocking method, the validity cycle method, and the number of times take effect at the same time. However, generally, only the following two situations are used:
For example, if you set to take effect from 8:00 to 8:30 in the morning from Monday to Friday during the period from 01/26/2018 at 08:00:00 to 08/08/2018 at 09:56:32, the validity is 0x 5A6A6F80 5B6A4DD0 02 0000001F 0800 081E:
01/26/2018 at 08:00:00 is converted to Unix time 1516924800, that is, 0x5A6A6F8008/08/2018 at 09:56:32 is converted to Unix time 1533693392, which is 0x5B6A4DD0